Vulnerability Found in WooCommerce Dynamic Pricing and Discounts
We have seen several stores infected with a vulnerability in the WooCommerce Dynamic Pricing and Discounts plugin in the last few weeks, so it is probably worth writing a few words about it.
In article:
Table of Contents
- The same problem again, allowing import without permissions.
- What is this vulnerability?
- How do attackers use this bug?
- I am using this plugin. What should I do?
- What are the general conclusions from the history of this vulnerability and attacks?
- Install plugins after prior security and usability analysis.
- Check and update any plugins on the website.
- How can I protect my website in the future?

The same problem again, allowing import without permissions.
The WooCommerce Dynamic Pricing and Discounts plugin from Envato is one of many plugins of this type. E-commerce businesses use it to set up dynamic prices and discounts for products based on various conditions. It’s hard to say why anyone would choose this particular plugin to use, as there are some great free alternatives out there. That said, the plugin has more than 20,000 purchases, making it a popular e-commerce plugin.
The WooCommerce Dynamic Pricing and Discounts plugin was created in 2014, and when browsing its changelog, you get the impression that it is constantly being developed and improved, with almost no bugs in it. The descriptions of the changes, however, are very laconic, and that never turns out well.
After seven years of the plugin’s existence, a critical vulnerability was detected on August 18, 2021. This vulnerability allows anyone to import settings with ease.
What is this vulnerability?
The authors of the plugin have created a settings import mechanism. However, they assumed that since the import option is only visible to the administrator, only the administrator can use it. The import code (class: “RP_WCDPD_Settings”, method: “__construct”) looks like this:
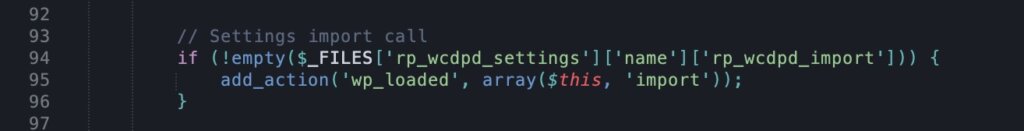
This fragment should already raise some doubts. If a file within the specified variable has been sent to the server, the import method is started automatically. It would be much better at this step to check whether the current user has the right to upload the file at all. What does the import method contain? Maybe it includes all the checks?
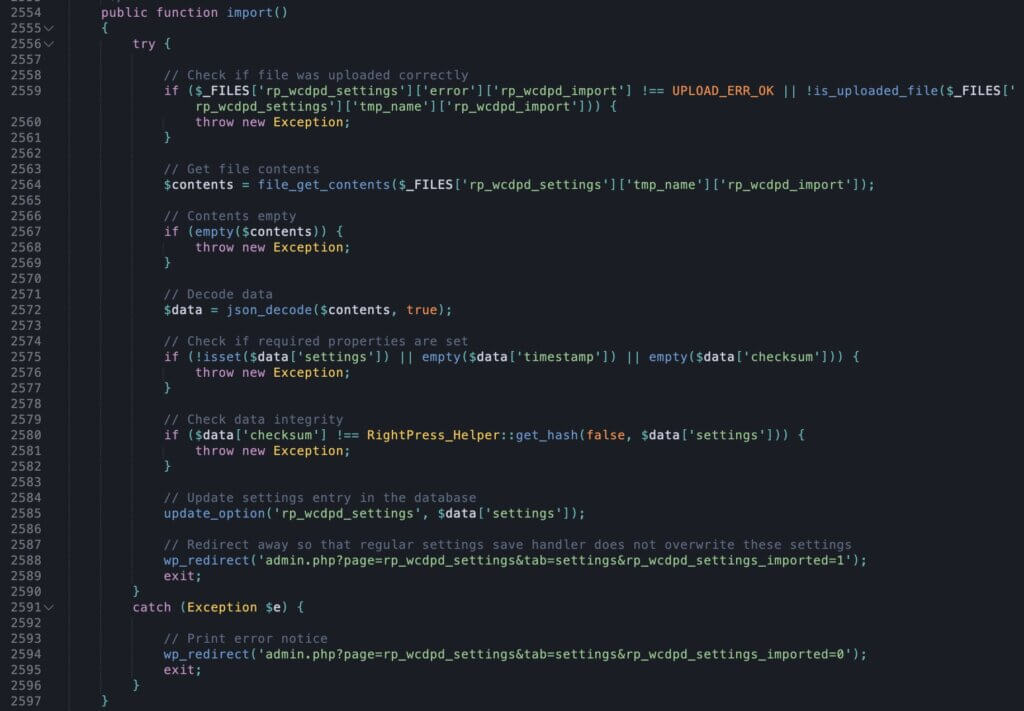
As you can see in the above code, there are unfortunately no checks here. The plugin is not checking:
- Whether the user has the right to update the settings,
- If anyone is logged in, and
- If the uploaded file contains the correct settings at all.
How do attackers use this bug?
We already know that all you need for the plugin to overwrite the settings we’ve chosen is to send a request containing a properly prepared file. This is already critical in the case of an online shop as it means the attacker can change the prices. For example, the attacker can set up a 100% discount on all products.
Unfortunately, like many plugins from Envato, this plugin is very extensive (has plenty of options). In addition to the discounts themselves, you can, among other things, set additional messages. And here another vulnerability appears. These messages are not escaped correctly. The combination of these two security bugs is used for attacks.
Settings that contain JS code are injected into the page. Code is then placed on the website and executed in the visitor’s browser.
In cases that came to us for malware removal, JavaScript was used to redirect store users to other websites. In another case, discounted prices turned up on products.
However, let’s not forget that the execution of JS code in the user’s browser also gives other possibilities (data theft, modification and eavesdropping of entered information, etc.).
I am using this plugin. What should I do?
On August 22, the plugin author released a fix that partially corrects the bug. In the importing function, a check has been added whether the current user has the right to modify the page settings.
Unfortunately, this is not sufficient and complete protection. To launch an attack, you must use a user account with the appropriate privileges. However, an XSS attack is still possible. Therefore, if the attacker prepares the proper request and executes it from the store owner’s browser, he will still be able to overwrite the settings. This process will require a lot more effort, however.
Given the above, my recommendations are:
- Update the plugin as a matter of urgency to make it impossible for anyone to attack, and
- Find an alternative to this plugin and change it.
If your website is infected and you have noticed that it has redirects, it will be necessary to have it cleaned. Contact us, we will remove the effects of the attack and secure the website.
What are the general conclusions from the history of this vulnerability and attacks?
Install plugins after prior security and usability analysis.
First of all, even paid plugins contain bugs (in my experience, much more often than free ones). Plugin authors often focus on functionality and capabilities rather than security. The features are sexy. You can boast about them, and they are selling. Security? Unfortunately, buyers ignore the security of plugins, and the authors can still make basic mistakes.
The selection of plugins mustn’t be made solely based on the description of functionality. It is also worth reviewing their changelogs and even assessing the quality of the code. This is the best way to be sure that the solution is proven and safe.
Check and update any plugins on the website.
The websites we cleaned from this infection were not attacked until September. Attacks happened after the revision had already been released. Unfortunately, that’s typical in these cases. The easiest way to find out about a plugin error is to monitor it and when the update is available, fix it.
If you were doing this, it would have been easy to protect yourself from infection. All you needed to do was keep the plugin up-to-date. If you want to read how to do plugin updates, read our article “Update, wait, ignore?” on 360WebCare.com.
All of the above reasons are why, as part of our Technical Support & Website Maintenance service, we monitor plugins and changes in their code on an ongoing basis. This allows us to react to critical vulnerabilities much faster and prevent exploitation. We also know the quality of a plugin’s code and can suggest a change or reduce the risk of attack by introducing additional fixes.
How can I protect my website in the future?
Do not be tempted to put off your WordPress website care – it can cost you much more in the long run. When issues accumulate, they can be harder to fix, and having a weak website can lead to more downtimes, costing you customers and conversions in the long run. It’s a much smarter business move and more cost-effective to have your website regularly checked on by an expert.